Microsoft SC-200 dumps are edited, reviewed and proven by Leads4Pass team of experts to help you pass the Microsoft Security Operations Analyst certification exam. They are updated throughout the year to keep it up to date! Download Microsoft SC-200 dumps: https://www.leads4pass.com/sc-200.html which contains 394 latest exam questions and answers to ensure you pass the exam on your first try.
Welcome to take the Microsoft SC-200 online practice test
| Number of exam questions | Compare Last Free Update |
| 15 | SC-200 dumps |
Question 1:
Your company stores the data for every project in a different Azure subscription. All the subscriptions use the same Azure Active Directory (Azure AD) tenant.
Every project consists of multiple Azure virtual machines that run Windows Server. The Windows events of the virtual machines are stored in a Log Analytics workspace in each machine\’s respective subscription.
You deploy Azure Sentinel to a new Azure subscription.
You need to perform hunting queries in Azure Sentinel to search across all the Log Analytics workspaces of all the subscriptions.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Add the Security Events connector to the Azure Sentinel workspace.
B. Create a query that uses the workspace expression and the union operator.
C. Use the alias statement.
D. Create a query that uses the resource expression and the alias operator.
E. Add the Azure Sentinel solution to each workspace.
Correct Answer: BE
Reference: https://docs.microsoft.com/en-us/azure/sentinel/extend-sentinel-across-workspaces-tenants
Question 2:
DRAG DROP
You have an Azure subscription that contains the users shown in the following table.
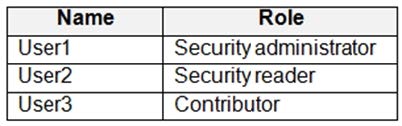
You need to delegate the following tasks:
1.
Enable Microsoft Defender for Servers on virtual machines.
2.
Review security recommendations and enable server vulnerability scans.
The solution must use the principle of least privilege.
Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
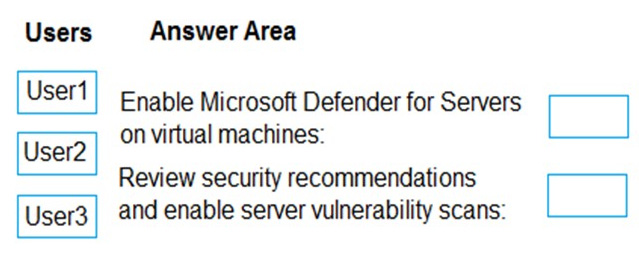
Correct Answer:
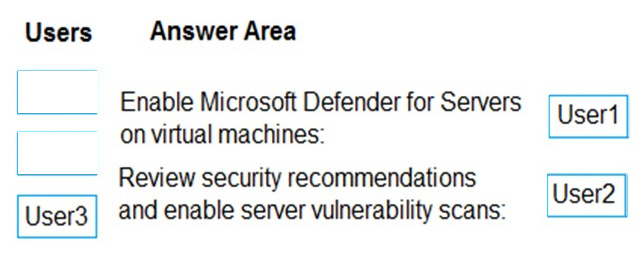
Box 1: User1
Enable Microsoft Defender for Servers on virtual machines.
User1 is Security Admin.
Security Admin
View and update permissions for Microsoft Defender for Cloud. Same permissions as the Security Reader role and can also update the security policy and dismiss alerts and recommendations.
Box 2: User2
Review security recommendations and enable server vulnerability scans.
User2 is Security Reader.
Security Reader
View permissions for Microsoft Defender for Cloud. Can view recommendations, alerts, a security policy, and security states, but cannot make changes.
Defender for Cloud\’s integrated Qualys vulnerability scanner for Azure and hybrid machines
Required roles and permissions:
Owner (resource group level) can deploy the scanner
Security Reader can view findings
Incorrect:
Contributor (User3)
Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC, manage assignments in Azure Blueprints, or share image galleries.
Reference: https://learn.microsoft.com/en-us/azure/role-based-access-control/built-in-roles https://learn.microsoft.com/en-us/azure/defender-for-cloud/deploy-vulnerability-assessment-vm
Question 3:
You have a Microsoft Sentinel workspace that has User and Entity Behavior Analytics (UEBA) enabled for Signin Logs. You need to ensure that failed interactive sign-ins are detected. The solution must minimize administrative effort. What should you use?
A. a scheduled alert query
B. the Activity Log data connector
C. a UEBA activity template
D. a hunting query
Correct Answer: C
Question 4:
HOTSPOT
You have a Microsoft 365 subscription that uses Microsoft 365 Defender and contains a user named User1.
You are notified that the account of User1 is compromised.
You need to review the alerts triggered on the devices to which User1 signed in.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
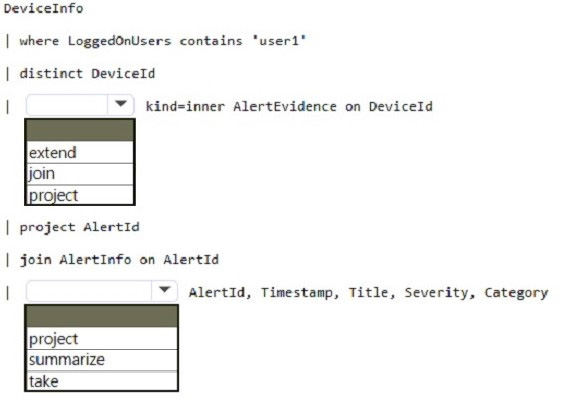
Correct Answer:
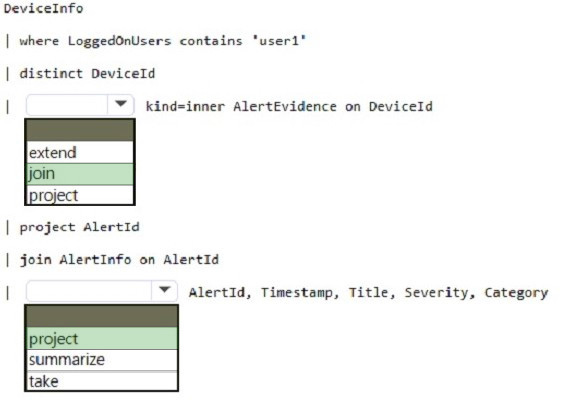
Box 1: join An inner join.
This query uses kind=inner to specify an inner-join, which prevents deduplication of left side values for DeviceId.
This query uses the DeviceInfo table to check if a potentially compromised user () has logged on to any devices and then lists the alerts that have been triggered on those devices. DeviceInfo //Query for devices that the potentially compromised account has logged onto | where LoggedOnUsers contains \’\’ | distinct DeviceId //Crosscheck devices against alert records in AlertEvidence and AlertInfo tables | join kind=inner AlertEvidence on DeviceId | project AlertId //List all alerts on devices that user has logged on to | join AlertInfo on AlertId | project AlertId, Timestamp, Title, Severity, Category DeviceInfo LoggedOnUsers AlertEvidence “project AlertID”
Box 2: project
Question 5:
You need to ensure that you can run hunting queries to meet the Microsoft Sentinel requirements. Which type of workspace should you create?
A. Azure Synapse Analytics
B. Azure Machine Learning
C. Log Analytics
D. Azure Databricks
Correct Answer: B
Fabrikam identifies the following Microsoft Sentinel requirements:
Run hunting queries on Pool1 by using Jupyter notebooks.
Get started with Jupyter notebooks and MSTICPy in Microsoft Sentinel
Run and initialize the Getting Started Guide notebook
This procedure describes how to launch your notebook and initialize MSTICpy.
1.
In Microsoft Sentinel, select Notebooks from the left.
2.
From the Templates tab, select A Getting Started Guide For Microsoft Sentinel ML Notebooks > Save notebook to save it to your Azure ML workspace.
3.
Etc.
Reference: https://learn.microsoft.com/en-us/azure/sentinel/notebook-get-started
Question 6:
You have an Azure subscription that uses Microsoft Defender for Cloud and contains a resource group named RG1. RG1. You need to configure just in time (JIT) VM access for the virtual machines in RG1. The solution must meet the following
1.
Limit the maximum request time to two hours.
2.
Limit protocol access to Remote Desktop Protocol (RDP) only.
3.
Minimize administrative effort. What should you use?
A. Azure AD Privileged Identity Management (PIM)
B. Azure Policy
C. Azure Front Door
D. Azure Bastion
Correct Answer: A
Question 7:
You have 500 on-premises Windows 11 devices that use Microsoft Defender for Endpoint.
You enable Network device discovery.
You need to create a hunting query that will identify discovered network devices and return the identity of the onboarded device that discovered each network device.
Which built-in function should you use?
A. SeenBy()
B. DeviceFromIP()
C. next()
D. current_cluster_endpoint()
Correct Answer: A
Question 8:
DRAG DROP
Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure AD tenant.
You have a Microsoft Sentinel workspace named Sentinel1.
You need to enable User and Entity Behavior Analytics (UEBA) for Sentinel1 and collect security events from the AD DS domain.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
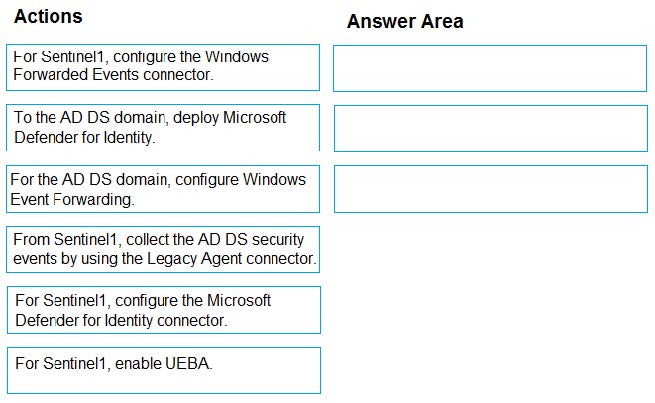
Correct Answer:
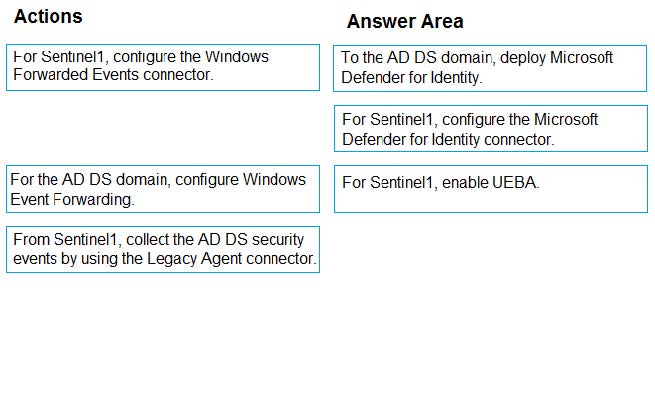
Step 1: To the AD DS domain, deploy Microsoft Defender for Identity
UEBA is integrated with Microsoft Sentinel through the use of the Microsoft Defender for Identity and Microsoft Cloud App Security connectors. These connectors allow UEBA data to be imported into Sentinel for analysis and investigation.
Step 2: For Sentinel1, configure the Microsoft Defender for Identity Connector
Step 3: For Sentinel1, enable UEBA
When you enable UEBA, it synchronizes your Azure Active Directory with Microsoft Sentinel, storing the information in an internal database visible through the IdentityInfo table in Log Analytics.
Note: How to enable User and Entity Behavior Analytics
1.
Go to the Entity behavior configuration page.
2.
On the Entity behavior configuration page, switch the toggle to On.
3.
Mark the check boxes next to the Active Directory source types from which you want to synchronize user entities with Microsoft Sentinel.
Active Directory on-premises (Preview)
Azure Active Directory
To sync user entities from on-premises Active Directory, your Azure tenant must be onboarded to Microsoft Defender for Identity (either standalone or as part of Microsoft 365 Defender) and you must have the MDI sensor installed on your
Active Directory domain controller.
4.
Mark the check boxes next to the data sources on which you want to enable UEBA.
5.
Select Apply. If you accessed this page through the Entity behavior page, you will be returned there.
Reference:
https://learn.microsoft.com/en-us/azure/sentinel/identify-threats-with-entity-behavior-analytics
https://learn.microsoft.com/en-us/azure/sentinel/enable-entity-behavior-analytics
Question 9:
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Microsoft Defender for Cloud and configure Defender for Cloud to use workspace1.
You need to collect security event logs from the Azure virtual machines that report to workspace1.
What should you do?
A. From Defender for Cloud, modify Microsoft Defender for Servers plan settings.
B. In sub1, register a provider.
C. From Defender for Cloud, create a workflow automation.
D. In workspace1, create a workbook.
Correct Answer: A
Question 10:
You have an Azure subscription that uses Microsoft Defender for Servers Plan 1 and contains a server named Server1.
You enable agentless scanning.
You need to prevent Server1 from being scanned. The solution must minimize administrative effort.
What should you do?
A. Create an exclusion tag.
B. Upgrade the subscription to Defender for Servers Plan 2.
C. Create a governance rule.
D. Create an exclusion group.
Correct Answer: A
Exclude machines from scanning Agentless scanning applies to all of the eligible machines in the subscription. To prevent specific machines from being scanned, you can exclude machines from agentless scanning based on your pre-existing environment tags. When Defender for Cloud performs the continuous discovery for machines, excluded machines are skipped.
To configure machines for exclusion:
1.
From Defender for Cloud\’s menu, open Environment settings.
2.
Select the relevant subscription or multicloud connector.
3.
For either the Defender Cloud Security Posture Management (CSPM) or Defender for Servers P2 plan, select Settings.
4.
For agentless scanning, select Edit configuration.
5.
Enter the tag name and value that applies to the machines that you want to exempt. You can enter multiple tag:value pairs.
6.
Select Save to apply the changes.
Note:
Defender for Servers Plan 1 is entry-level and must be enabled at the subscription level.
Features include:
Foundational cloud security posture management (CSPM), which is provided free by Defender for Cloud.
Defender for Servers Plan 2 provides all features. The plan must be enabled at the subscription level and at the workspace level to get full feature coverage. Features include:
All the functionality that\’s provided by Defender for Servers Plan 1.
More extended detection and response (XDR) capabilities. Reference:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/enable-agentless-scanning-vms#exclude-machines-from-scanning https://learn.microsoft.com/en-us/azure/defender-for-cloud/plan-defender-for-servers-select-plan
Question 11:
You are configuring Azure Sentinel.
You need to send a Microsoft Teams message to a channel whenever an incident representing a sign-in risk event is activated in Azure Sentinel.
Which two actions should you perform in Azure Sentinel? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Enable Entity behavior analytics.
B. Associate a playbook to the analytics rule that triggered the incident.
C. Enable the Fusion rule.
D. Add a playbook.
E. Create a workbook.
Correct Answer: BD
Reference: https://docs.microsoft.com/en-us/azure/sentinel/enable-entity-behavior-analytics https://docs.microsoft.com/en-us/azure/sentinel/automate-responses-with-playbooks
Question 12:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Prevent future attacks section.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
You need to resolve the existing alert, not prevent future alerts. Therefore, you need to select the `Mitigate the threat\’ option.
Question 13:
HOTSPOT
You have an Azure Storage account that will be accessed by multiple Azure Function apps during the development of an application.
You need to hide Azure Defender alerts for the storage account.
Which entity type and field should you use in a suppression rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
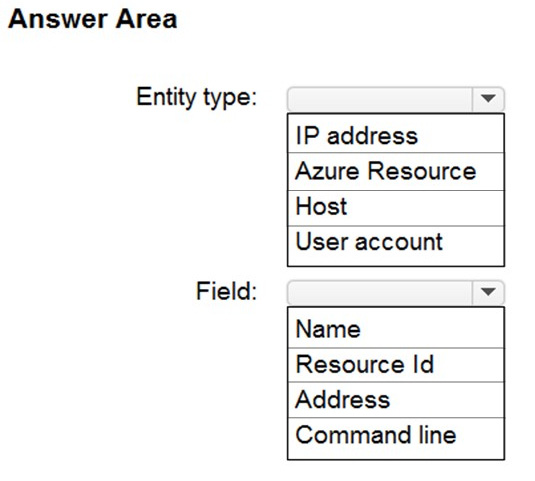
Correct Answer:
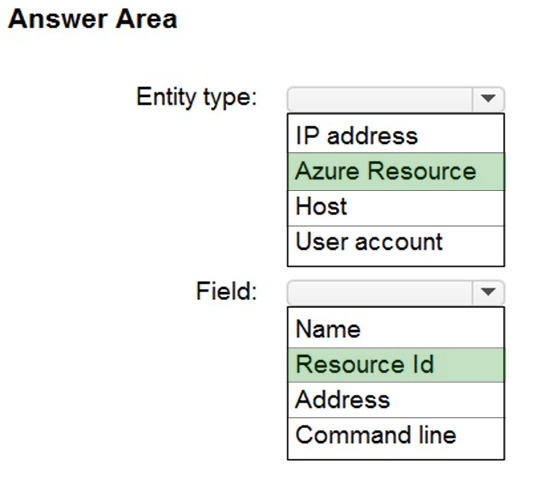
Question 14:
You need to ensure that the configuration of HuntingQuery1 meets the Microsoft Sentinel requirements. What should you do?
A. Add HuntingQuery1 to a livestream.
B. Create a watch list.
C. Create an Azure Automation rule.
D. Add HuntingQuery1 to favorites.
Correct Answer: D
Question 15:
HOTSPOT
You have on-premises servers that run Windows Server.
You have a Microsoft Sentinel workspace named SW1. SW1 is configured to collect Windows Security log entries from the servers by using the Azure Monitor Agent data connector.
You plan to limit the scope of collected events to events 4624 and 4625 only.
You need to use a PowerShell script to validate the syntax of the filter applied to the connector.
How should you complete the script? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
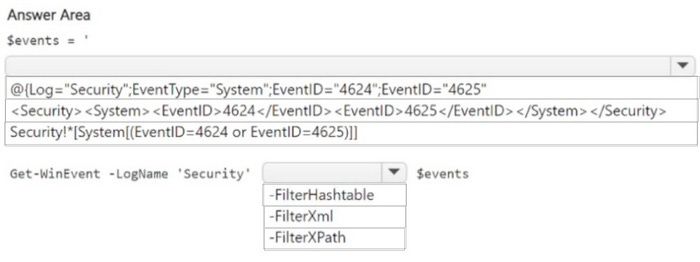
Correct Answer:
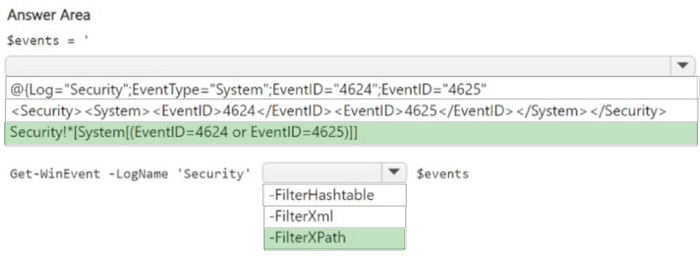
…
See the complete list of Microsoft SC-200 dumps
The above shares a set of the latest Microsoft SC-200 dumps exam practice questions for 2025 for free for you to experience in advance.
Please check out the latest complete list of SC-200 dumps exam questions for 2025:
| Total Q&As | 394 |
| Single & multiple choice | 230 |
| Drag drop | 35 |
| Hotspot | 129 |
| Testlet | 4 |
Summarize
Microsoft SC-200 dumps contains 394 latest exam questions and answers. Welcome to use SC-200 dumps with PDF and VCE simulation engine: https://www.leads4pass.com/sc-200.html to help you practice test efficiently and prepare for Microsoft Security Operations Analyst certification exam.